Certificate Authority (CA) Chain, can be also referred to as CA bundle, is a set of intermediate and root certificates used to establish the connection between a certificate issued for a domain name (end-entity certificate) and a Certificate Authority that issued the certificate.
The end-entity certificate is signed by the intermediate certificate (subordinate CA), which in its turn is signed by a root certificate, or another intermediate certificate signed by root.
Root certificates are generated by Certificate Authorities. They are embedded into the software applications, browsers and operating systems and their installation on the server is not mandatory in most cases.
Your web browsers will automatically trust the certificate if they succeed to track the chain of trust to the root certificate. The root certificate is a starting point in this chain of trust and is considered a trust anchor.
Root certificates sign intermediate certificates. The latter ones serve as a link between the Certificate Authority and the website certificate. When a user browses to the website protected by the SSL certificate via secure connection, the browser initiates the verification of the certificate and follows the chain of trust up to the root certificate embedded in it. Intermediate certificate(s) should be installed on the server, along with the end-entity certificate, for the certificate to be recognized as a trusted one in all browsers.
To check the CA chain installation you can use various online checking tools like:
SSL Certificate Checker
Online checking tools, as a rule, show whether the certificate is trusted, or if some elements of the chain of trust are missing.
If you have a Linux machine with openssl package installed on the server, you can use the following command for verification:
openssl s_client -connect example.com:443
If there are more than one SSL certificate installed on one IP address, you will need to add -servername example.com flag.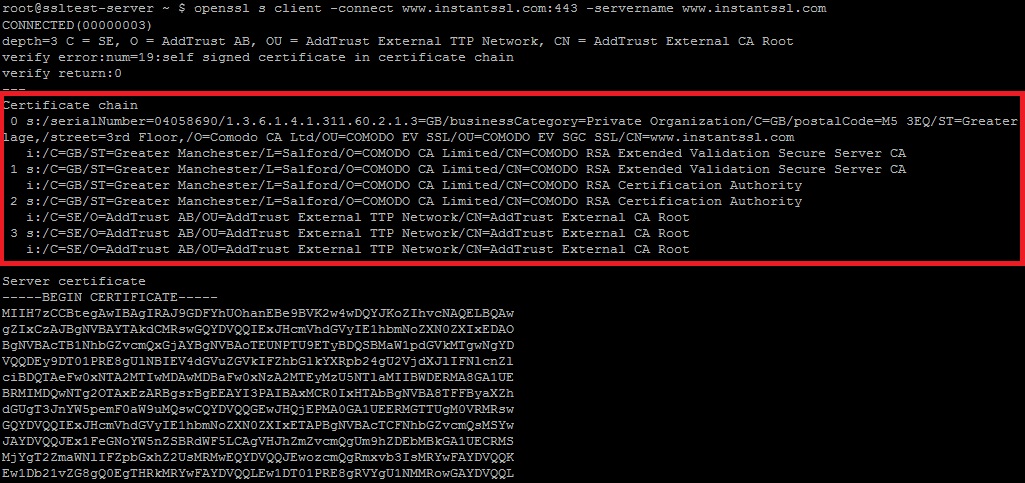
The chain of trust starting from the end-entity certificate will be shown in the 'Certificate chain' section.
Below you will find the list of all intermediate and root certificates in the correct order for SSLs we provide. It will help you in checking the CA chain installation and in proper combining the CA bundle files for the SSL installation on the server.
COMODO Domain Validation Certificates (PositiveSSL, PositiveSSL Wildcard, PositiveSSL Multi-Domain, EssentialSSL, EssentialSSL Wildcard):
- Intermediate 2: COMODO RSA Domain Validation Secure Server
- Intermediate 1: COMODO RSA Certification Authority
- Root: Add Trust External CA Root
- Intermediate 2: COMODO RSA Organization Validation Secure Server CA
- Intermediate 1: COMODO RSA Certification Authority
- Root: Add Trust External CA Root
COMODO Extended Validation Certificates (EV SSL, EV SGC SSL, EV Multi-Domain SSL):
- Intermediate 2: COMODO RSA Extended Validation Secure Server CA
- Intermediate 1: COMODO RSA Certification Authority
- Root: Add Trust External CA Root
