Before you start the SSL installation process, please make sure that the CSR code is generated, all validation requirements are met, and the SSL certificate is issued and downloaded from ZTABOX email.
The next prerequisites are intended to ease SSL installation and help you avoid the common pitfalls:
- Having access to the hosting server configuration over SSH via the terminal.
- The website should be working over the HTTP connection (default port 80)
- The private key should be located and matched with the SSL certificate. Check this article to find the private key and match it with the SSL certificate using this tool.
As you may know, there are many Linux distributions where an Apache HTTP server can be installed. In this article, we will review SSL installation steps for two major operating system families: Debian-based and RHEL-based ones.
Debian, Ubuntu
For an Apache web server to run an encrypted HTTPS connection, make sure that the SSL mode is enabled by using this command:
sudo a2enmod ssl
Upload the SSL certificate files (.crt and .ca-bundle) to your server to the /etc/ssl/ folder and move the private key file (.key) to /etc/ssl/private/ for your convenience.
To start the SSL installation, locate the Apache configuration file which contains < VirtualHost *:80 >...< /VirtualHost > settings for the HTTP connection of your website.
The default location of this file may vary and depends on the server configuration and the OS version.
In most cases, the appropriate configuration file (symbolic link) for the enabled HTTP website can be found in the /etc/apache2/sites-enabled/ directory for Debian and Ubuntu OS.
The following command may be helpful to find the proper configuration file:
apachectl -S
The output may display a port (80), domain name (example.com), the conf file path (/etc/apache2/sites-enabled/000-default.conf) and line number (1) where Virtual Host for the HTTP connection starts.
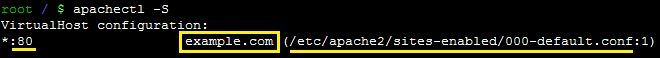
The next output indicates that Apache already has a configuration file for a secure HTTPS connection, so you need to update it according to the SSL renewal section.
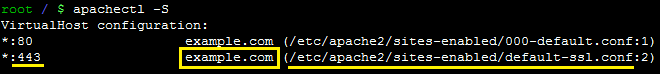
If you do not see the configuration file for secure connection (*:443 line with your domain name), a new SSL installation is required. Follow these instructions:
Make a replica of the configuration file where Virtual Host settings for the HTTP connection is located. This command may be helpful:
cp /etc/apache2/sites-available/your_website.conf
/etc/apache2/sites-available/your_website-ssl.conf
Note! A new configuration file should be created in the sites-available directory.
Open the new configuration file with any text editor, change the port to 443 (default for the HTTPS connection) and add SSL directives. The example of a new Virtual Host for 443 may look like:
< VirtualHost *:443 >
ServerName example.com
DocumentRoot /var/www/
SSLEngine on
SSLCertificateFile /etc/ssl/example_com.crt
SSLCertificateKeyFile /etc/ssl/private/example_com.key
SSLCertificateChainFile /etc/ssl/example_com.ca-bundle
< /VirtualHost >
Note! Starting from Apache 2.4.8, the 'SSLCertificateChainFile' directive became obsolete. Intermediate certificates (CA bundle) can be added to the 'SSLCertificateFile' right after the certificate code.
Enable the new SSL configuration file by running this command:
sudo a2ensite your_website-ssl.conf
When a new VirtualHost is created, save the file and run the syntax check:
apachectl -t
If the system shows 'Syntax OK', reload the Apache for the changes to make effect with the following command:
sudo service apache2 reload
Should any syntax error appears, it will be shown right away for troubleshooting.
The SSL installation can be verified using these tools: here or here
To save the SEO ranking, it is recommended redirecting all HTTP requests to the secure HTTPS version of your website permanently.
Note! If you are using a multi-domain or wildcard certificate, it is necessary to modify the configuration files for each domain/subdomain for which the SSL certificate is issued, unless this domain is used as ServerAlias. You would need to specify the domain/subdomain you need to secure and refer to the same certificate files in the VirtualHost record the way described above.
CentOS, Fedora, Red Hat Enterprise Linux (RHEL)
For an Apache web server to run an encrypted HTTPS connection, make sure that mod_ssl is installed with the help of this command:
sudo yum install mod_ssl
Upload the SSL certificate files (.crt and .ca-bundle) to your server to /etc/pki/tls/certs/ folder and move your private key .key to /etc/pki/tls/private/ for your convenience.
To start the SSL installation, locate the Apache configuration file which contains < VirtualHost *:80 >...< /VirtualHost > settings for the HTTP connection of your website.
The default location of this file may vary and depends on the server configuration and the OS version.
In most cases, the appropriate settings for the HTTP website can be found in /etc/httpd/conf/httpd.conf file for CentOS, Fedora, RHEL OS.
The following command may be helpful to locate the proper configuration file:
httpd -S
The output may display a port (80), domain name (example.com), the conf file path (/etc/httpd/conf/httpd.conf) and line number (355) where Virtual Host for the HTTP connection starts.
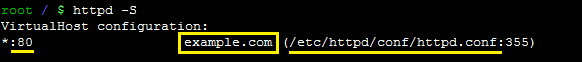
The next output indicates that Apache already has a configuration file for a secure HTTPS connection, so you need to update it according to the SSL renewal section.
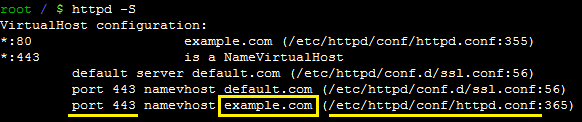
If you do not see a line for port 443 with your domain name, create a replica of the Virtual Host block for port 80 in the same configuration file, change the port to 443 (default for the HTTPS connection) and add SSL directives. The example of a new VirtualHost for 443 may look like:
< VirtualHost *:443 >
ServerName example.com
DocumentRoot /var/www/
SSLEngine on
SSLCertificateFile /etc/pki/tls/certs/example_com.crt
SSLCertificateKeyFile /etc/pki/tls/certs/example_com.key
SSLCertificateChainFile /etc/pki/tls/certs/example_com.ca-bundle
< /VirtualHost >
Note! Starting from Apache 2.4.8, the 'SSLCertificateChainFile' directive became obsolete. Intermediate certificates (CA bundle) can be added to the 'SSLCertificateFile' right after the certificate code.
When the new VirtualHost is created, save the file and run the syntax check:
httpd -t
If the system shows 'Syntax OK', reload Apache for the changes to make effect with the following command:
sudo service httpd reload
Should any syntax error appears, it will be shown right away for troubleshooting.
The SSL installation can be verified using these tools: here or here
To save the SEO ranking, it is recommended redirecting all HTTP requests to the secure HTTPS version of your website permanently.
Note! If you are using a multi-domain or wildcard certificate, it is necessary to modify the configuration files for each domain/subdomain for which the SSL certificate is issued, unless this domain is used as ServerAlias. You would need to specify the domain/subdomain you need to secure and refer to the same certificate files in the VirtualHost record the way described above.
SSL renewal
SSL Renewal instructions are slightly different and can be useful when any SSL certificate has been installed for this website before. To obtain new SSL certificate with prolonged expiration date, make sure that all renewal steps are completed.
As soon as you have renewal SSL certificate files (.crt and .ca-bundle), upload them to your hosting server and locate the Apache configuration file containing current HTTPS settings of the website as described on the screenshots for your operating system above.
Open this file with any text editor and update the paths to the new certificate, ca-bundle and private key files within the server block < VirtualHost *:443 >...< /VirtualHost > with ServerName for your domain.
When the existing VirtualHost is updated, save the file and run the syntax check:
apachectl -t (Debian, Ubuntu, etc.)
httpd -t (RHEL, CentOS, etc.)
If the system shows 'Syntax OK', reload Apache for the changes to make effect with the following command:
sudo service apache2 reload (Debian, Ubuntu, etc.)
sudo service httpd reload (RHEL, CentOS, etc.)
The SSL installation and new expiration date can be verified using these tools: here or here
